All Posts / What Is Threat Modelling and How Does it Minimise Cyber Security Risk?
Cyber security
What Is Threat Modelling and How Does it Minimise Cyber Security Risk?

As cyber hazards continue to escalate, businesses need to be proactive.
They have to protect their sensitive data and assets from cybercriminals. Threats to data security are constant and come from many different places.
These days, offices feature sophisticated digital technologies. Nearly every activity depends in some way on technology and data sharing. There are several ways for hackers to access these systems. This includes PCs, smartphones, cloud apps, and network infrastructure.
Cybercriminals are thought to be able to access 93% of business networks. Threat modelling in cybersecurity is one strategy that can assist enterprises in fending off these incursions. One procedure used in cybersecurity is threat modelling. It entails determining possible dangers and weak points in the resources and systems of an organization.
Businesses can better prioritize their risk management and mitigation initiatives with the use of threat modelling. Reducing the likelihood of becoming a victim of an expensive cyber disaster is the aim.
What is Threat Modeling?
Threat modelling is the process of obtaining, assembling, and assessing all of this data.
It facilitates well-informed decision-making regarding application security threats when applied to software. Typical threat modelling efforts yield a prioritized list of security enhancements to be made to an application’s idea, requirements, design, or implementation in addition to a model.
The Threat Modeling Manifesto was developed in 2020 by a group of threat modelling practitioners, authors, and researchers with the intention of “…sharing a distilled version of our collective threat modelling knowledge in a way that should inform, educate, and inspire other practitioners to adopt threat modelling as well as improve security and privacy during development.” The Manifesto offers ideas and concepts connected to these themes, along with patterns and anti-patterns to aid in the adoption and practice of Threat Modeling.
Benefits of Threat Modeling
- Early problem detection in the SDLC
Organizations can save money and effort by preventing expensive and time-consuming solutions later in the development process by recognizing potential risks and vulnerabilities at the design stage. Instead of trying to add security as an afterthought, this proactive strategy enables firms to integrate security into their systems from the ground up.
Early detection of any problems also allows engineers to fix them in their code. This may result in more secure software and help prevent the need for costly and disruptive fixes or updates down the road.
To put it simply, threat modelling can assist in transforming security from a reactive to a proactive process.
- Consider novel ways of attacking
With the ongoing evolution of cybersecurity, new risks and attack vectors are appearing. Threat modelling offers an organized method for locating and evaluating these ever-evolving dangers, enabling organizations to stay one step ahead of them.
Organizations may keep up with the most recent security threats and vulnerabilities by routinely upgrading their threat models. To stay ahead of the current threats, they can use this to modify their security plans and defences in reaction to the shifting threat landscape.
- Determine the security needs.
Organizations can identify the security controls they need to implement to safeguard their assets by comprehending potential system risks and the potential consequences of failing to maintain a strong security posture.
To guarantee that the system is constructed with security in mind from the beginning, these security needs should be integrated into the system design and development process. Systems may become more secure as a result, and businesses may be able to prevent expensive and disruptive security breaches. Building channels of communication between IT, Security, and Development is essential for ensuring company continuity and developing disaster recovery plans since security is frequently overlooked.
- Map controls, threat actors, and assets
Security leadership and risk teams can better understand what they need to protect, who would want to attack it, and how to defend it by developing a detailed model of the fundamental components of the most important business systems throughout the company. Prioritizing the implementation of controls over the web interface, APIs, and back-end databases is necessary, for example, if the company operates a transactional website. Maintaining service accounts and ICS while limiting external access of any kind may be crucial for a manufacturing company.
By concentrating on the most important assets and threats, this understanding can assist businesses in prioritizing their security efforts and resources. Additionally, it can offer a precise implementation roadmap for security controls, assisting businesses in making sure their systems and data are adequately safeguarded.
Threat Modeling Processes and Methodologies
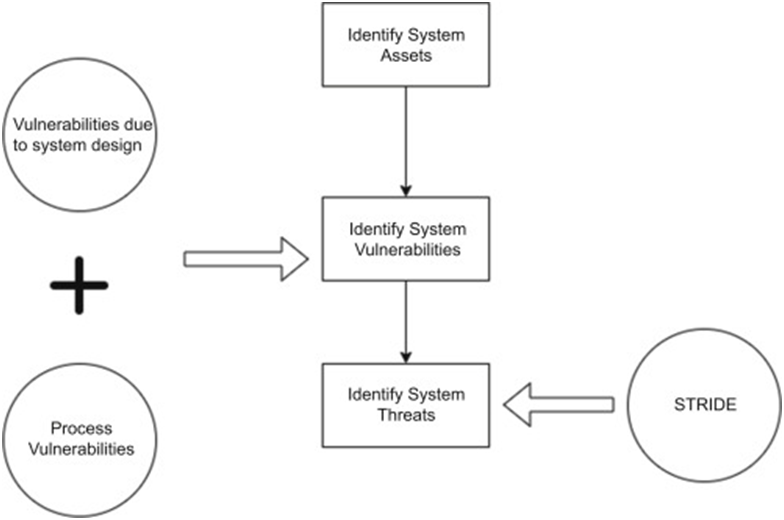
1. STRIDE
Spoofing, tampering, repudiation, informational disclosure, denial of service (DoS), and elevation of privilege are often referred to as STRIDE.

2. DREAD
DREAD stands for Damage potential, reproducibility, exploitability, affected users, and discoverability.
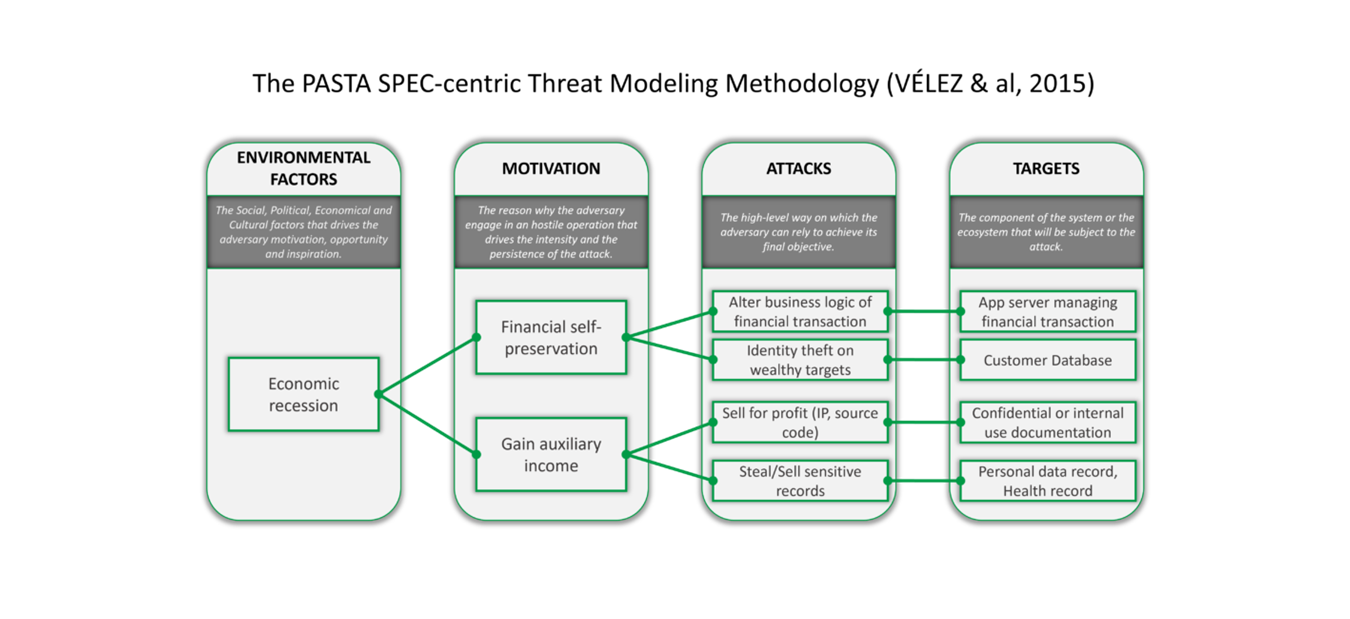
3. PASTA
Threat Analysis and Attack Simulation Process (PASTA)
PASTA is a seven-step, attacker-centric technique.
4. Visual, Agile, and Simple Threat (VAST)
Based on the ThreatModeler platform, Visual, Agile, and Simple Threat (VAST) is an automated threat modelling technique. Big businesses use VAST throughout their whole infrastructure to retain scalability and produce dependable, actionable outcomes.
5. Trike
Threat modelling approaches are used in the Trike security audit framework to manage risk and defend against attacks. After Trike specifies a system, an analyst creates a requirement model by listing all of the system’s actors, assets, rules, and actions.
6. OCTAVE
Operationally Critical Threat Asset and Vulnerability Evaluation is referred to as OCTAVE. Carnegie Mellon University designed it.
7. NIST
The National Institute of Standards and Technology, or NIST for short, has created a data-driven threat modelling system of its own.
How to Minimize Your Cybersecurity Risk Using Threat Modeling
Businesses need to take proactive steps to protect their sensitive data and precious assets from malevolent hackers in the face of an increasing spike in cyber threats. With the increasing digital complexity of today’s businesses, where almost every task involves technology and data interchange, data security threats continue to arise from a variety of sources.
Hackers use a variety of entry points, including cloud apps, smartphones, desktops, and network infrastructure, with a startling 93% chance of breaking into business networks.
Businesses use threat modelling to prioritize risk management and mitigation methods to effectively address these risks. The ultimate goal is to reduce the possibility of being a victim of a cyberattack that causes financial damage.
The procedure for conducting a thorough threat model by firms is outlined in the following sections.
1. Determine Which Assets Require Security
The first step is to identify the most important assets for the company, which include financial data, intellectual property, and sensitive data. These are the main targets for thieves looking to make big money. It is important to remember that phishing-related assets, such as corporate email accounts, are being used more frequently in the rapidly expanding Business Email Compromise (BEC) attack. Attacks of this kind thrive on exploiting hacked workplace email accounts.
2. Determine Possible Threats
In the next phase, we concentrate on identifying any risks that might compromise these resources. Cyberattacks, which include phishing, ransomware, malware, and social engineering tactics, are among the most common risks.
Other types of hazards exist as well, like insider risks and physical breaches, in which workers or vendors gain access to private data. It’s crucial to remember that threats don’t always originate from malevolent intent; over 88% of data breaches are the result of human error. As a result, it’s critical to stay alert to dangers associated with mistakes, like using flimsy passwords, ambiguous cloud usage guidelines, inadequate staff training and inadequate or nonexistent BYOD guidelines.
3. Evaluate the Impact and Likelihood
The next stage after identifying potential risks is to assess each threat’s likelihood and potential repercussions. Businesses must get a thorough comprehension of the probability of occurrence and the possible consequences for their operations, image, and financial stability.
To prioritize risk management and mitigation techniques, this evaluation is essential. Current cybersecurity data and a comprehensive vulnerability assessment—ideally carried out by a reliable third-party IT service provider—should be the basis for the assessment. An external perspective is crucial since relying exclusively on internal input for the assessment could cause significant features to be missed.
4. Give Risk Management Strategies Top Priority
The next item on the agenda is to rank the risk management solutions according to the probability and consequences of each possible danger. Ranking the solutions based on how much of an impact they have on cybersecurity becomes essential, given the time and financial constraints that the majority of enterprises confront. This strategy optimizes resource allocation by concentrating efforts on resolving the most serious risks first.
Among the typical tactics to think about are putting into practice:
- Controls over access
- Protective barriers
- Systems for detecting intrusions
- Programs for employee awareness and training
- Device management on endpoints
Companies also need to figure out which tactics are the most economical. They should also be in line with their corporate objectives.
5. Review and update the model regularly
The process of threat modelling is dynamic and ongoing due to the constant evolution of cyber threats. To ensure that their security measures are successful and in line with their business goals, businesses need to regularly assess and update their threat models. They can keep up with changing threats and preserve a strong cybersecurity posture by doing this.
Table of contents
Related Posts
We’ll handle the tech
so you can get on with
running your business.

CALL US
1300 414 214
Our Trusted Partners
Contact Us
Let’s Talk
Common Questions
Do you outsource your work overseas?
No. We use local teams only. That way we can respond more quickly to any problems that may occur. We want your tech running smoothly so you can focus on what you do best.
Is your support 24 hours?
Yes. We have people available whenever you need us. We understand that your tech runs 24 hours, and you need it be working at all times.
Are your services customised for my business?
Yes. There is great off the shelf software. But we know one size never fits all. So anything we set up for you is designed to make your business run smoother and in the way you want it to.
Are your services expensive?
No. Reliable tech is the life blood of your business. We keep it running smoothly so your business can keep making money. All our services are fixed fees, so you never get any nasty surprises.
What’s the next step?
Simply book a chat with one of our experts. We’ll have a chat about exactly what you need and how we can help. If you like our approach then we’ll give you a fixed price quote and get everything up and running for you, fast!