All Posts / What Is An MSSP? An Expert Guide – Telco ICT Group
Cyber security
What Is An MSSP? An Expert Guide – Telco ICT Group

Are you trying to find a way to keep secure online with your businesses? Have you heard of managed security service providers but are unsure about what they entail or how to safeguard the data of your company?
Managed Security Service Providers, or MSSPs like Telco ICT Group, offer a range of security services including patch management, risk assessments, and monitoring.
This gives organizations the confidence that their information systems are safe at all times is the aim of a cyber security company.
Internet service providers marked the beginning of MSSP history in the late 1990s (ISPs).
Around that time, a few ISPs started to offer firewall equipment to their customers, and if the customer wanted, the ISP would even take care of the firewall. The foundation of the MSSP is this managed firewall solution, which is incorporated into ISPs’ service offerings.
The idea of the specialist MSSP developed over time, and companies began to offer outsourced security services on a specific basis. The services provided by an MSSP expanded to become full-service security providers in tandem with the growth of the cyber threat landscape and businesses’ security requirements.
What is an MSSP (Managed Security Service Provider)
Businesses can obtain a comprehensive outsourced security solution from managed security service providers.
An excellent MSSP will offer endpoints, cloud-based infrastructure, and networks for an organization’s security monitoring, disaster recovery, and incident response.
It’s critical to comprehend not just what a cyber security provider provides, but also the situations in which you might need their services. Your security system and device management and monitoring are outsourced when you outsource your cyber security protection and monitoring.
When your outsourced cybersecurity provider manages all of your vital technological systems, your IT teams will have more time to work on other initiatives that will help you achieve your company goals.
It’s essential to comprehend not just what an MSSP is but also how they’re utilized. When you use an MSSP, you are outsourcing the management and watchful eye over security devices and systems. IT teams can focus on other projects that advance company goals when vital security systems are under the control of an outside party.
Typical these services consist of:
1. Managed firewall
A managed firewall is a type of service that employs security specialists to implement enhanced threat management. These experts keep a close eye on your firewall and take action in the event of a threat.
Hiring a watchman, policeman, and detective all at once is analogous to using a managed firewall. The network traffic on your system is closely examined to look for and identify trends. Security parameters are formed by these patterns.
A warning is sent out and the possible threat is dealt with when an occurrence deviates from these parameters.
2. Antivirus Services
Every year, there is an increase in the variety of viral attacks, and IT teams frequently find it challenging to stay on top of the growing pool of potential threats. With its resources, an MSSP can focus on the viruses that are most likely to cause immediate harm to your network and its users. After that, the MSSP can create a portfolio of Antivirus services that target the most noticeable dangers. Furthermore, network-wide Antivirus actions can be taken at different nodes and locations. Antivirus solutions, for instance, can be set up to satisfy the security requirements of internal servers, and distinct solutions can be created for cloud servers.
3. Intrusion detection
Networks are traditionally likened to castles. It is theoretically possible to protect everything you value inside with a sufficiently large moat. Nevertheless, contemporary intrusion detection entails analyzing every part, individual, and piece of software—whether it is within or outside the “castle.” A competent MSSP will safeguard all systems and devices and ensure that malicious actors cannot use them to compromise other systems within or outside of your company. This is known as intrusion detection.
4. Vulnerability scanning
An MSSP looks for weaknesses in your network in addition to identifying possible attacks, which is a crucial step. Occasionally, these contain places of business and confidential information, which are prime targets for online fraudsters. In other situations, a weakness two or three degrees away from a target can be used to breach locations or systems that thieves wish to access. Whether a vulnerability is within, next to, or a few degrees distant from an attack surface, an MSSP can identify it.
5. Virtual private network (VPN)
An MSSP can set up a VPN to safely conceal the activities of your company. The attack surface is greatly reduced by a private VPN since it is protected from outside intervention. Your MSSP only needs to put network security protocols in place to protect the network from those users and their devices if only the necessary users are allowed access to the VPN.
What is the Difference between MSSPs and MSPs (Managed Service Providers)
Third-party companies that offer services to a business are known as managed service providers (MSPs) and managed security service providers (MSSPs). The aim of these two categories of service providers, however, is very different. In addition to providing standard network and IT support, an MSP offers services including Security as a Service (SaaS) platforms and managed telephony (telco). An MSSP, on the other hand, is just concerned with offering security services.
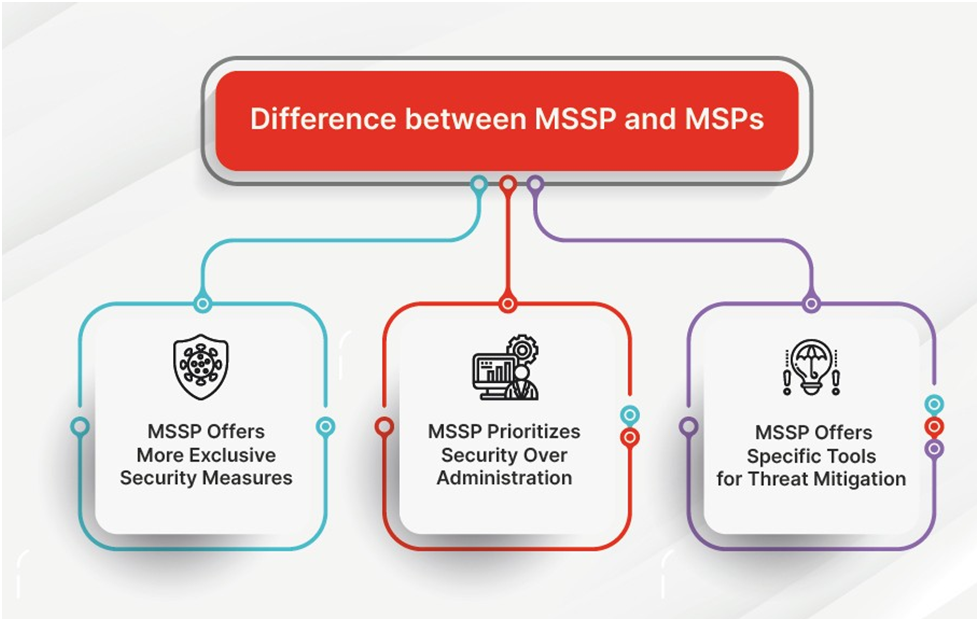
The “operations centre” of an MSP and an MSSP is one of their obvious distinctions. A network operations centre (NOC), where an MSP oversees and manages the networks of its clients, is probably in operation. A security operations centre (SOC), which offers 24-hour security monitoring and incident response, ought to be run by an MSSP.
Benefits of MSSPs for Your Business
The purpose of an MSSP is to supplement or replace the internal security team within a business. A business that partners with an MSSP can gain several advantages:
1. Enhanced posture in cybersecurity
Elevating cybersecurity posture is foundational to organizational resilience. Initiating this process involves a comprehensive evaluation of the current security landscape, allowing entities to assess their risk profile and identify potential vulnerabilities for exploitation by malicious actors.
Identification of weaknesses prompts proactive measures, including regular system patching, the implementation of robust passwords, and the adoption of multi-factor authentication (MFA) for enhanced user account security.
Adopting proactive threat management practices is pivotal for organizations seeking to fortify their security postures. This involves the incorporation of cybersecurity services such as threat detection and response, security monitoring, incident response, and Security Information and Event Management (SIEM) solutions.
Through these measures, organizations can significantly reduce the risk of security breaches while adhering to cybersecurity best practices.
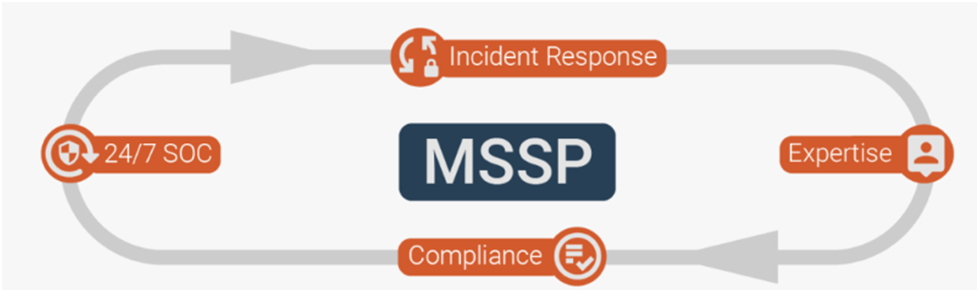
2. Prowess in Proactive Threat Management
Proactivity in cyber threat management forms a cornerstone of robust IT security plans. This approach encompasses the utilization of diverse tools to identify, prevent, and mitigate network threats before they can manifest harm. Key steps in proactive threat management include:
- Establishing a baseline: Understanding regular activity is crucial for identifying malicious behaviour.
- Continuous monitoring: Regular scrutiny of log files and data sources for suspicious activity or unusual patterns is vital for breach detection.
- Implementing safeguards: Employing technologies like firewalls, antivirus software, and intrusion detection systems (IDS) shields against known vulnerabilities and potential attacks.
- Ongoing education: Ensuring staff is well-versed in the latest security best practices and procedures facilitates prompt recognition of potential risks and appropriate action. This will contribute well to your compliance management efforts as it ensures your team is in the loop with the new regulations etc.
3. Optimal Cost-Effectiveness Through MSSPs
Managed Security Service Providers (MSSPs) offer comprehensive cybersecurity packages at competitive prices. This presents a cost-effective alternative to internal IT staffing or outright software license purchases.
By bundling various services together, MSSPs enable businesses to achieve long-term cost savings.
Additionally, selecting a Cyber Security Provider not only saves time and money but also ensures the implementation of high-quality security measures against cyber threats.
The expertise of MSSPs contributes to the growth and protection of businesses, making them a valuable asset in the cybersecurity landscape. To maximize these benefits, careful consideration is necessary when choosing the right MSSP tailored to the specific needs of a business.
Conclusion
MSSPs like Telco ICT Group offer security services, including:
- Vulnerability assessments
- Incident response and support
- Threat intelligence and monitoring
- Incident response
These services assist businesses in staying up to date on the most recent risks and implementing precautionary measures.
Additionally, you can start with managed detection and response(MDR). This is a situation when a company contracts with a third-party service to handle portions of its security operations. This ensures that you have experts helping you while you still have control over your whole security operation.
Furthermore, in the event of a security incident, Telco ICT may offer firms support and experience to help them respond efficiently and lessen the damage of the assault.
Telco ICT ensures that businesses can feel more at ease knowing that their security is under the care of qualified experts just as we did with these businesses.
Call us today!
Table of contents
Related Posts
We’ll handle the tech
so you can get on with
running your business.

CALL US
1300 414 214
Our Trusted Partners
Contact Us
Let’s Talk
Common Questions
Do you outsource your work overseas?
No. We use local teams only. That way we can respond more quickly to any problems that may occur. We want your tech running smoothly so you can focus on what you do best.
Is your support 24 hours?
Yes. We have people available whenever you need us. We understand that your tech runs 24 hours, and you need it be working at all times.
Are your services customised for my business?
Yes. There is great off the shelf software. But we know one size never fits all. So anything we set up for you is designed to make your business run smoother and in the way you want it to.
Are your services expensive?
No. Reliable tech is the life blood of your business. We keep it running smoothly so your business can keep making money. All our services are fixed fees, so you never get any nasty surprises.
What’s the next step?
Simply book a chat with one of our experts. We’ll have a chat about exactly what you need and how we can help. If you like our approach then we’ll give you a fixed price quote and get everything up and running for you, fast!