All Posts / Intrusion Detection and Prevention Systems (IDPS): Enhancing Firewall Security
Cyber security
Intrusion Detection and Prevention Systems (IDPS): Enhancing Firewall Security

In a world where technological advancements drive businesses forward, the threat landscape for cyberattacks is ever-expanding.
As organizations increasingly rely on digital infrastructure, the need for robust cybersecurity measures becomes paramount.
The first line of defence, firewalls, while crucial, is not impervious to the relentless innovation of cybercriminals. This is where the Intrusion Detection and Prevention Systems (IDPS), come in as the dynamic guardians of network security.
As cyber threats evolve, so must our defence mechanisms. IDPS emerges as a linchpin in the cybersecurity arsenal, offering a multifaceted approach to fortify defences.
From advanced threat detection and real-time monitoring to incident response and risk mitigation, IDPS plays a pivotal role in safeguarding digital assets.
Intrusion Detection and Prevention System: What is it? How does It work?
An intrusion detection and prevention system (IDPS) is a system that keeps an eye out for potential security breaches on a network and responds appropriately.
An intrusion detection system and an IDPS are closely related (IDS). An IDPS works to counteract threats in addition to detecting them and alerting users about them.
An intrusion prevention system (IPS) is another name for an IDPS. Although the terms IDPS and IPS are frequently used interchangeably, when an IPS is mentioned, it’s usually about the IDPS’s threat-hunting capability.
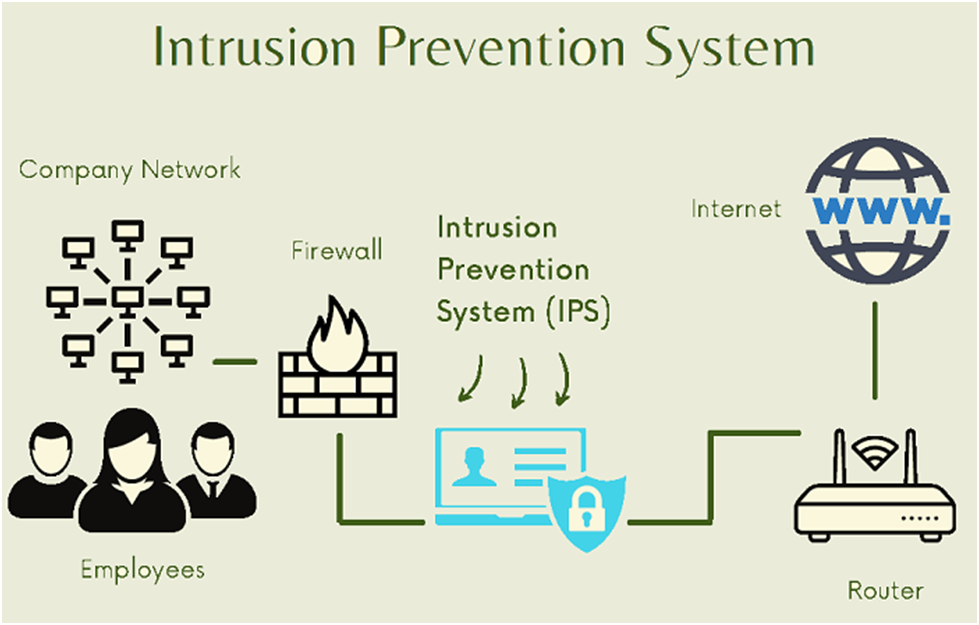
How does IDPS work?
Businesses today rely entirely on technology for everything from communication to server hosting of applications. The attack surface that cybercriminals can exploit grows as technology advances.
According to a CheckPoint study from 2021, there were 50% more weekly attacks on business networks in 2021 than there were in 2020. As a result, businesses of all sizes and industry verticals are strengthening their security posture to defend their digital infrastructure from cyberattacks at every level.
The first line of defence against unsolicited and suspect traffic entering a system is a firewall. It is easy to believe that hostile traffic cannot penetrate a firewall and that firewalls are 100% secure. But cybercriminals never stop developing new ways to get around security systems.
An intrusion detection and prevention system can help in this situation. The IDPS controls what passes through the system, while a firewall controls what enters. It frequently operates in tandem with firewalls directly behind them.
An intrusion detection and prevention system functions similarly to airport security and luggage check-in. When entering an airport, travellers must provide their ticket or boarding permit, and they cannot board their aircraft until all mandatory security procedures have been completed.
Similar to this, an intrusion detection system (IDS) just keeps an eye out for rule violations or malicious traffic. It was the forerunner of the intrusion detection and prevention system, or intrusion prevention system (IPS).
With automated courses of action, the IPS not only monitors and alerts but also attempts to avert potential incidents.
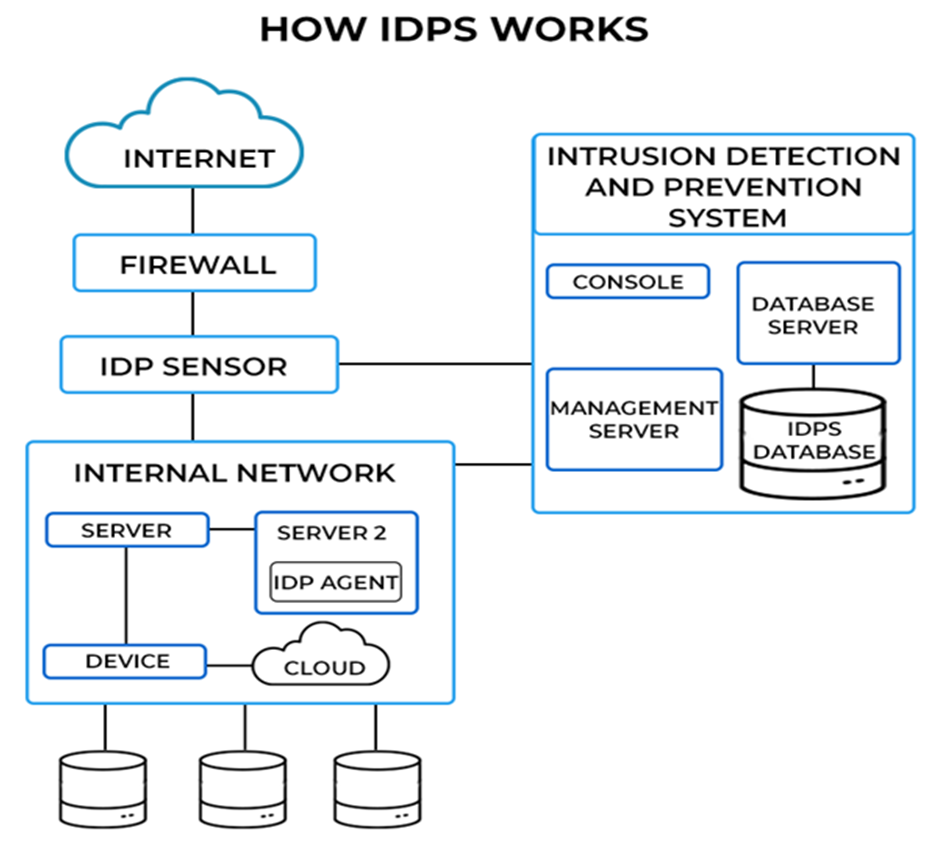
IDPS Types:
1. Network-based IDPS
Installed at specified locations inside a network, network-based IDPS (NIPS) is a type of IDPS designed to monitor network traffic and identify potential risks.
A security professional manually configures a database of known threats, which is compared to activity analysis by the NIPS. Proceeding via the network is prohibited if the behaviour is identified in the database as a known danger.
In routers, modems, firewalls, and network remote access points, among other network boundary locations, a Network Intrusion Prevention System (NIP) is frequently installed.
NIPS is divided into two subcategories:
- Wireless intrusion prevention systems (WIPS): By examining the radio frequencies of a wireless network, wireless intrusion prevention systems (WIPS) keep an eye out for rogue access points and unidentified devices. Wireless networks and areas susceptible to unwanted wireless access are equipped with WIPS.
- Network behaviour analysis (NBA) systems: Systems that analyze network behaviour (NBA) scan network traffic for anomalous activity patterns. To overwhelm a network, hundreds of requests are delivered in a distributed denial of service attack (DDOS). All of these requests, while seemingly reasonable on their own, point to a larger issue. NBA systems frequently support a more conventional NIPS on the internal networks of a company.
2. IDPS based on the host
Host-based IDPS (HIPS) are installed on a single host, which is usually a public server that serves as a gateway to an organization’s internal network or a crucial server that houses vital data. Specifically, a HIPS keeps an eye on the flow of traffic on its host system. Typically, host operating system activity and internet protocol suite (TCP/IP) activity are detected by HIPS.
IDPS Features at the Prevention Level
1. Neutralizing the attack
Intrusion prevention technology, sometimes referred to as “banishment vigilance,” stops problems before they start. This is accomplished by preventing users or traffic coming from a specific IP address. Resetting or ending a network connection is another aspect of it. For instance, it makes sense to deny access until these requests are looked into if a specific user is scanning data too frequently.
2. Changes in the security environment
To stop assaults, this entails modifying security setups. Reconfiguring the firewall settings to prohibit a certain IP address is an example of how the IPS works.
3. Attacks involving altered content
A system can be compromised by malicious material in several ways. Eliminating the offensive sections is one method to make this information more benign. A simple example would be deleting emails with attachments that seem suspicious. Repackaging incoming payloads to a common, pre-designed lot—for example, by deleting extraneous header information—is a more complex example.
What are the IDPS benefits?
As the cybersecurity landscape evolves, organizations face constant threats to their digital assets. In this environment, having robust Intrusion Detection and Prevention Systems (IDPS) is paramount. IDPS offers a multifaceted approach to fortify your defences. This is by combining advanced threat detection, real-time monitoring, and rapid incident response. In this section, we’ll look into the myriad benefits of IDPS.
1. Intrusion Detection Alerts
An IDPS is instrumental in providing timely and accurate intrusion detection alerts. It does this by analyzing network and system activities, it identifies unusual patterns or behaviours that may indicate a security breach. The timely detection of such anomalies enables organizations to respond swiftly, minimizing potential damage and preventing unauthorized access.
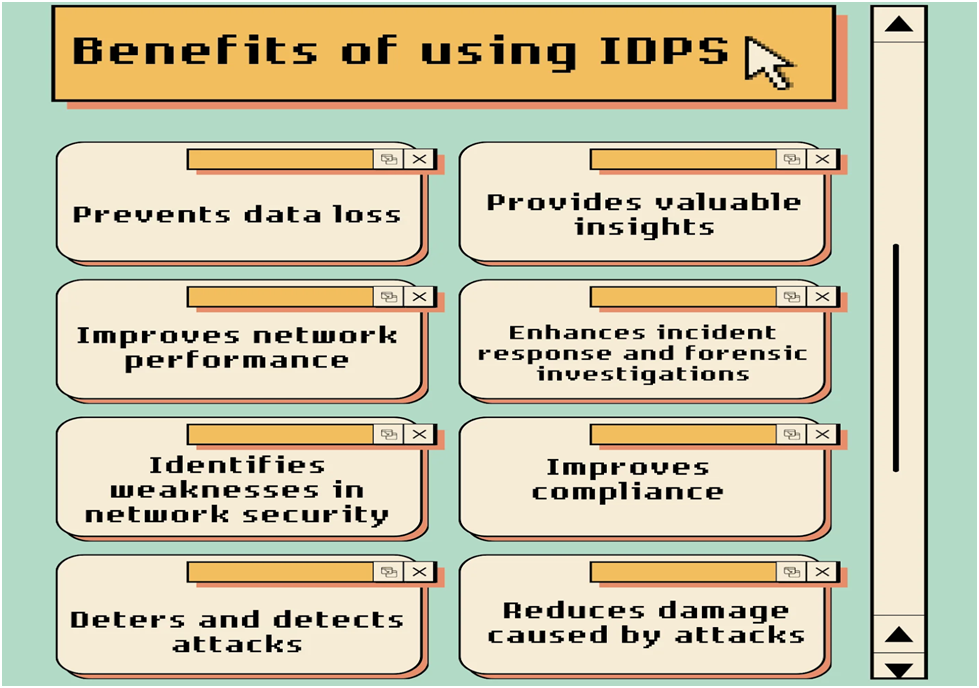
2. The IDPS Architecture thoroughly analyzes the traffic
The architecture of an IDPS is designed for network traffic analysis and monitoring, leveraging a combination of signature-based and anomaly-based detection methods. Signature-based detection relies on known patterns of malicious activity, while anomaly-based detection identifies deviations from normal behaviour. This dual approach enhances the system’s accuracy in identifying both known and emerging threats.
3. Threat Intelligence Integration
Integrating threat intelligence into IDPS by far enhances its effectiveness. It ensures that the system stays abreast of the latest threats and attack vectors and hence proactively defends against evolving cyber threats. This integration ensures that the system is not solely reliant on historical data but is continuously updated to recognize and counter emerging threats.
4. Cybersecurity Risk Mitigation
By identifying and stopping harmful activity, IDPS are essential in cybersecurity threat detection. The probability of successful cyberattacks is considerably decreased by its capacity to recognize vulnerabilities and take immediate action. Being proactive helps to lower cybersecurity risk overall by safeguarding private information and preserving the integrity of digital assets.
5. Real-Time Network Monitoring
An essential component of IDPS functioning is real-time monitoring. Through persistent observation of network activity, the system can promptly detect and react to irregularities. This real-time strategy is essential for reducing the effects of cyber threats and stopping illegal access before it gets worse.
6. Security Incident Response
IDPS is essential to incident response since it offers accurate and up-to-date information on security occurrences. This makes it possible for businesses to react to security events quickly, minimizing damage and starting the necessary corrective actions. An organization’s overall cybersecurity resilience is improved through the integration of IDPS with incident response procedures.
7. Network Anomaly Detection
The ability to detect anomalies in network behaviour is a key strength of IDPS. By establishing a baseline of normal activity, the system can swiftly identify deviations that may indicate a security breach. This anomaly detection capability is crucial for identifying previously unknown threats and preventing their impact.
Conclusion
When it comes to the discussion of IDPS vs. Firewalls, the distinction lies in their primary functions and focus within the cybersecurity framework. Firewalls serve as the initial gatekeepers, concentrating on preventing unauthorized access and regulating traffic at the network perimeter based on predefined rules.
On the other hand, IDPS operates within the network, specializing in the detection and response to potential security breaches, whether originating externally or occurring internally.
While firewalls establish the first line of defence by controlling access, IDPS acts as a vigilant guardian, actively monitoring for and responding to various types of malicious activities within the network.
Together, IDPS and firewall integration form a complementary collaboration that creates a comprehensive defense strategy, crucial in navigating the complexities of today’s evolving threat landscape.
Table of contents
Related Posts
We’ll handle the tech
so you can get on with
running your business.

CALL US
1300 414 214
Our Trusted Partners
Contact Us
Let’s Talk
Common Questions
Do you outsource your work overseas?
No. We use local teams only. That way we can respond more quickly to any problems that may occur. We want your tech running smoothly so you can focus on what you do best.
Is your support 24 hours?
Yes. We have people available whenever you need us. We understand that your tech runs 24 hours, and you need it be working at all times.
Are your services customised for my business?
Yes. There is great off the shelf software. But we know one size never fits all. So anything we set up for you is designed to make your business run smoother and in the way you want it to.
Are your services expensive?
No. Reliable tech is the life blood of your business. We keep it running smoothly so your business can keep making money. All our services are fixed fees, so you never get any nasty surprises.
What’s the next step?
Simply book a chat with one of our experts. We’ll have a chat about exactly what you need and how we can help. If you like our approach then we’ll give you a fixed price quote and get everything up and running for you, fast!