Being ready for cybersecurity threats is one of the biggest challenges that businesses face today.
Even with the growing emphasis on making Melbourne’s business IT security strong, there are still several widespread misconceptions about cybersecurity in the business community.
Being ready for cybersecurity threats is one of the biggest challenges that businesses face today.
Even with the growing emphasis on making businesses cyber-safe, there are still several widespread misconceptions about cybersecurity misconceptions in the business community.
If any of the following beliefs are accepted by you or your staff, your company may be exposed to unidentified danger. In this blog, we are debunking IT security myths and helping you maintain the cybersecurity of your company.
Top 10 Most Common Security Myths in Melbourne
1. Only Certain Industries are Vulnerable to Cyber Attacks
Similar to how some companies think their size will protect them from attacks, some companies mistakenly think that their industry will shield them from attacks.
This myth is closely related to the idea that certain businesses don’t have anything that would be “worth” stealing.
In actuality, any sensitive information—including addresses, credit card numbers, and personal data—can make a company a target.
Furthermore, the data being targeted might be essential for the operation of the company even if it has no market value on the dark web.
For instance, ransomware can obliterate data unless you pay for a decryption key. Even if the data is considered to be of “low value,” cybercriminals may find attacks to be quite profitable as a result.
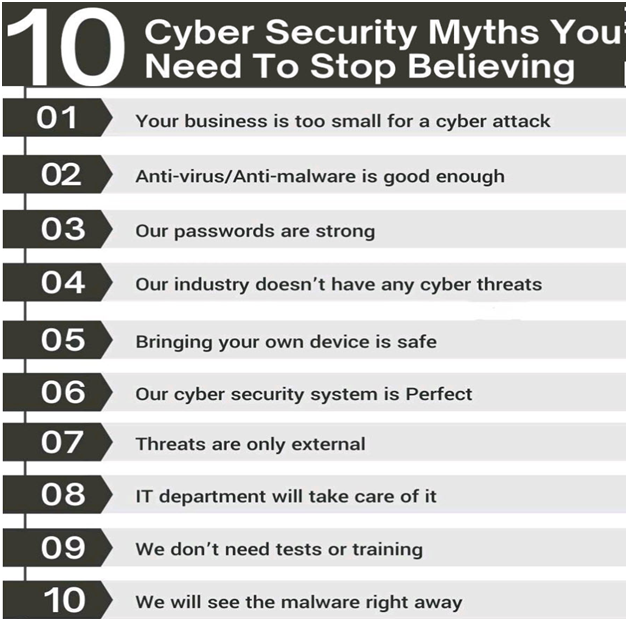
2. Anti-virus and Anti-malware software keep your Company Safe
Antivirus software is unquestionably crucial to maintaining the security of your company, but it cannot shield you from all threats.
Software is only the first step in an all-encompassing cybersecurity strategy. You need a comprehensive solution that covers everything.
It needs to cover insider threat detection and disaster recovery to employee training to properly safeguard your company.
3. The Business Size Matters
Due to the frequent coverage of high-profile hacks in the media, small and medium-sized firms are frequently led to believe that they are not going to be attacked.
In actuality, the reverse is true. Small firms account for 58% of data breach victims, according to the 2018 Verizon Data Breach Investigations Report.
There are various reasons why this occurs. Many businesses are the victims of “spray-and-pray” attacks, in which hackers set up automated systems to randomly enter businesses, rather than being directly targeted. Due to the random nature of these strikes, businesses of any size are susceptible to damage.
Small firms are often “softer” targets. This is because they lack the resources to purchase sophisticated business data protection software. Additionally, small businesses often do not have well-trained security teams. This makes them more vulnerable to spray-and-pray attacks. Due to their lack of protection, small enterprises are frequently the target of targeted attacks.
4. Melbourne Small Business Cyber Threats Come From the Outside
This is not nearly true. Studies indicate that up to 75% of data breaches may be caused by insider threats.
Insider threats should also be closely observed, as they pose an equal threat to safety as external ones and should be closely monitored.
It’s crucial to have a mechanism in place to prevent and keep an eye on insider threats. This is because they can originate from anybody on the inside. It can include content staff lacking the necessary cybersecurity knowledge and irate employees seeking professional retribution.
5. IT security for Businesses is solely the IT department’s responsibility
The IT department bears a significant portion of the responsibility for developing and monitoring the regulations that firms need to follow to stay safe online. But even so, everyone in the organization must be prepared for cybersecurity threats.
For instance, 49% of malware, according to Verizon, is installed via email.
Employees who lack cybersecurity best practices training, such as identifying phishing scams and avoiding dangerous links, may be exposing your business to risks.
6. Wi-Fi Password Makes it Secure
Employees who travel frequently, work remotely, or share workspaces may mistakenly believe that a Wi-Fi network is secure if they work for your company.
The main purpose of Wi-Fi passwords is to restrict the number of users on a network—other users who may have the same password may be able to read the private information being communicated. To increase the security of their data, these personnel ought to purchase VPNs.
7. If your System is Infected, You’ll Know Immediately
It may have been true ten or so years ago that you could tell right away if your computer was infected with a virus. Indicators such as pop-up advertisements, browsers that took a long time to load, and, in severe situations, complete system crashes were common.
But the malware of today is far more cunning and difficult to identify.
Your compromised machine may continue to function normally, allowing the virus to cause damage for a while before being discovered.
This of course depends on the strain your computer or network is infected with.
8. You can Achieve Complete IT security
The fight against cybersecurity is never-ending; it’s not a chore to be completed and then forgotten.
Your system and data are constantly at risk from new malware and attack techniques. You must regularly monitor your systems, carry out internal audits, and examine, test, and assess your contingency plans if you want to be genuinely cyber-safe.
Maintaining a company’s cyber safety involves ongoing work and the involvement of all employees.
If any employees at your organization have fallen for one of the aforementioned myths, it might be time to reconsider your cybersecurity training and do a risk assessment audit of your business.
9. Personal Devices are Not a Threat at Work
Workers frequently believe that the security measures that the company applies to its computers do not apply to their devices.
Bring Your Own Device (BYOD) guidelines have thereby exposed businesses to cyber risks that they might not be aware of. Workers must adhere to the same policies implemented on all network computers when using their personal devices for work-related tasks.
These regulations extend beyond computers and cell phones. All internet-accessible gadgets, including wearables and other Internet of Things devices, should be covered by BYOD policies.
10. We have Great Technology, We are Safe
This is an incorrect and smug way of thinking. You’re not protected just because your company has the newest cyber-security measures in place.
You are still vulnerable to hacking despite everything. Around half of the cyberattacks that were disclosed in 2015 were the result of employee negligence or insider theft.
Your company needs three layers of cyber-protection to be practically hacker-proof: the newest hardware, the most recent software, and cyber-security protocols ingrained in your company culture.
Conclusion
These myths about Melbourne’s cybersecurity best practices pose a real risk to companies in the current digital environment. Believing them makes businesses oblivious to actual threats and facilitates the work of cybercriminals.
Acquiring a solid security plan begins with realizing that these cybersecurity myths are false beliefs that do more harm than good.
Furthermore, setting up the right protocols is now simpler than ever thanks to artificial intelligence security technologies, which make your security smarter and more automatic.
With any luck, this list of the top 10 cybersecurity fallacies you should dispel will put you on the right track toward building a safe and developed company.
Table of contents
Related Posts
We’ll handle the tech
so you can get on with
running your business.

CALL US
1300 414 214
Our Trusted Partners
Contact Us
Let’s Talk
Common Questions
Do you outsource your work overseas?
No. We use local teams only. That way we can respond more quickly to any problems that may occur. We want your tech running smoothly so you can focus on what you do best.
Is your support 24 hours?
Yes. We have people available whenever you need us. We understand that your tech runs 24 hours, and you need it be working at all times.
Are your services customised for my business?
Yes. There is great off the shelf software. But we know one size never fits all. So anything we set up for you is designed to make your business run smoother and in the way you want it to.
Are your services expensive?
No. Reliable tech is the life blood of your business. We keep it running smoothly so your business can keep making money. All our services are fixed fees, so you never get any nasty surprises.
What’s the next step?
Simply book a chat with one of our experts. We’ll have a chat about exactly what you need and how we can help. If you like our approach then we’ll give you a fixed price quote and get everything up and running for you, fast!